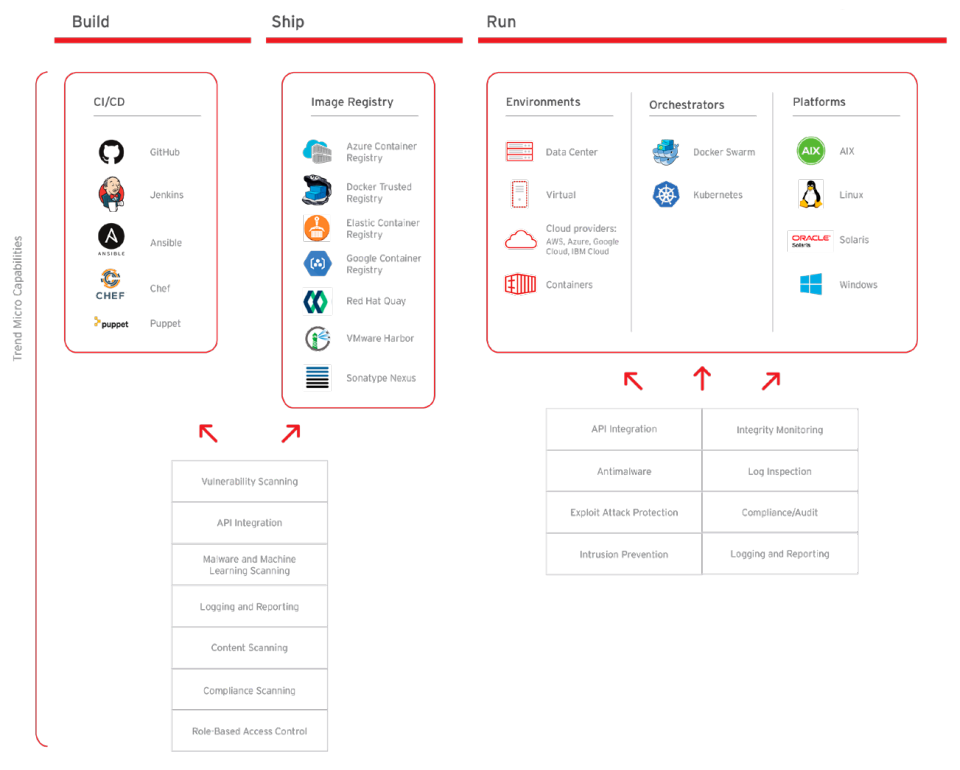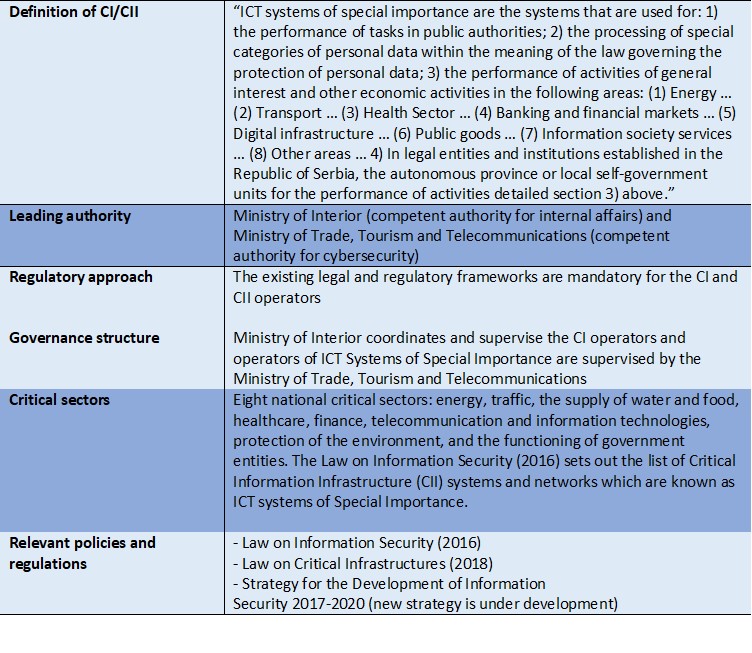
Enhancing the protection and cyber-resilience of critical information infrastructure | Digital Regulation Platform

VxBlock System key values extended to CI data protection | Protect Your Data Wherever it Lives: A Data-First Strategy for Fully Integrated VxBlock Systems | Dell Technologies Info Hub

PDF) Policy Based Management for Critical Infrastructure Protection | Michel Riguidel - Academia.edu
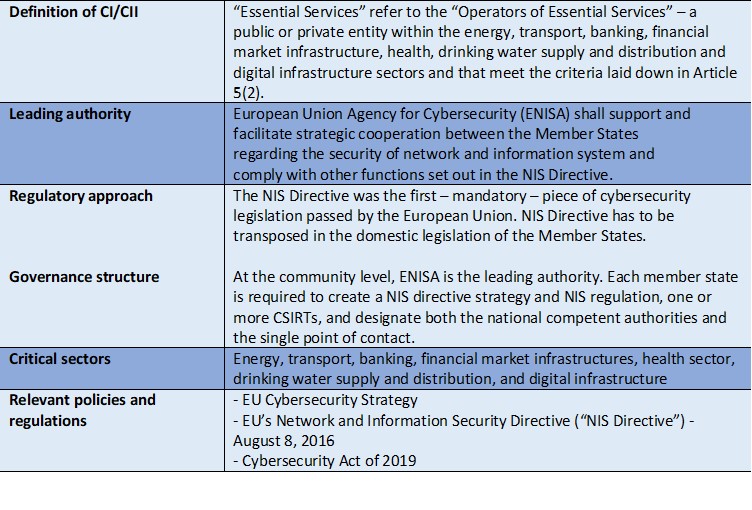
Enhancing the protection and cyber-resilience of critical information infrastructure | Digital Regulation Platform
Hoffman A1001YZUMC1 1001, Class 1 Small-Volume Type Y and Z Purging/Pressurization System | Southern Electronics

Energies | Free Full-Text | Selected Issues Associated with the Operational and Power Supply Reliability of Fire Alarm Systems
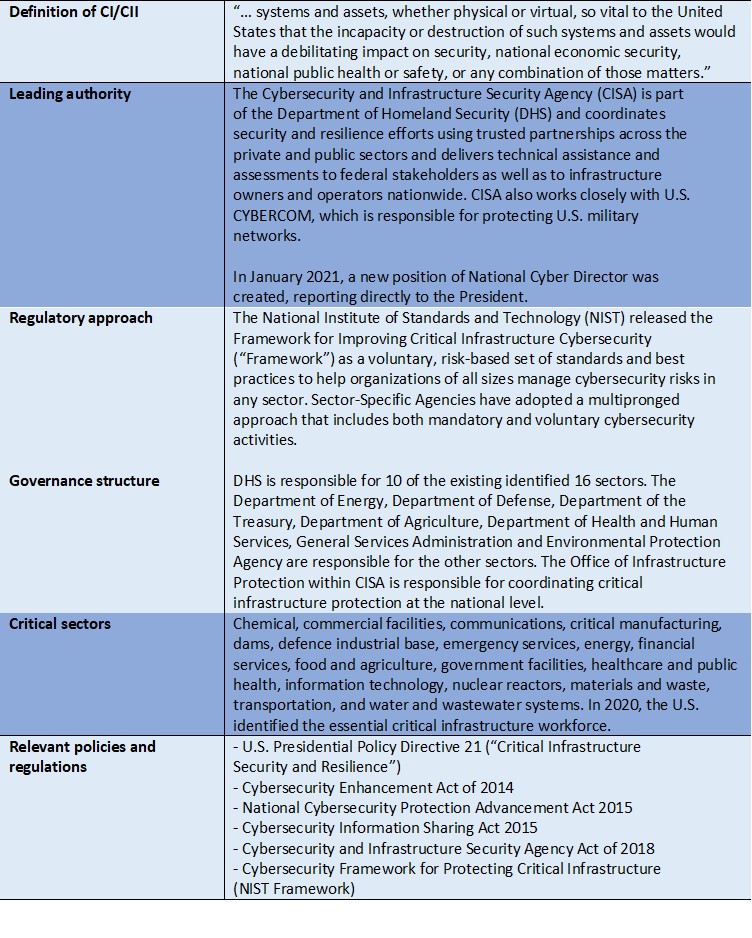
Enhancing the protection and cyber-resilience of critical information infrastructure | Digital Regulation Platform
Regulatory Guide 1.206 - Section C.I.8, Electrical Power, to Combined License Applications for Nuclear Power Plants (LWR Edition

Information Security Systems vs. Critical Information Infrastructure Protection Systems - Similarities and Differences | Semantic Scholar
Figure4.1: Context Diagram Fig 4.1 illustrates various access control... | Download Scientific Diagram