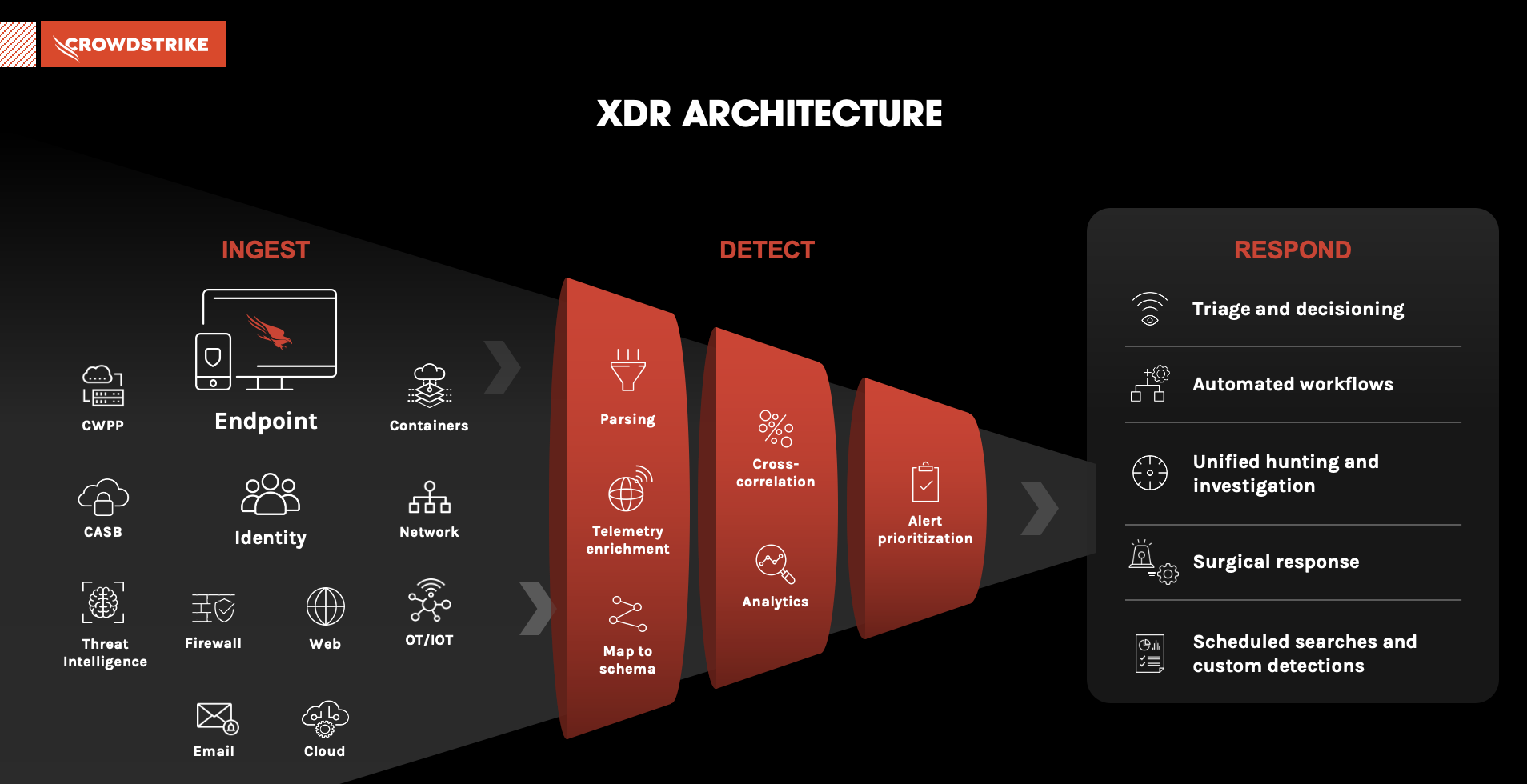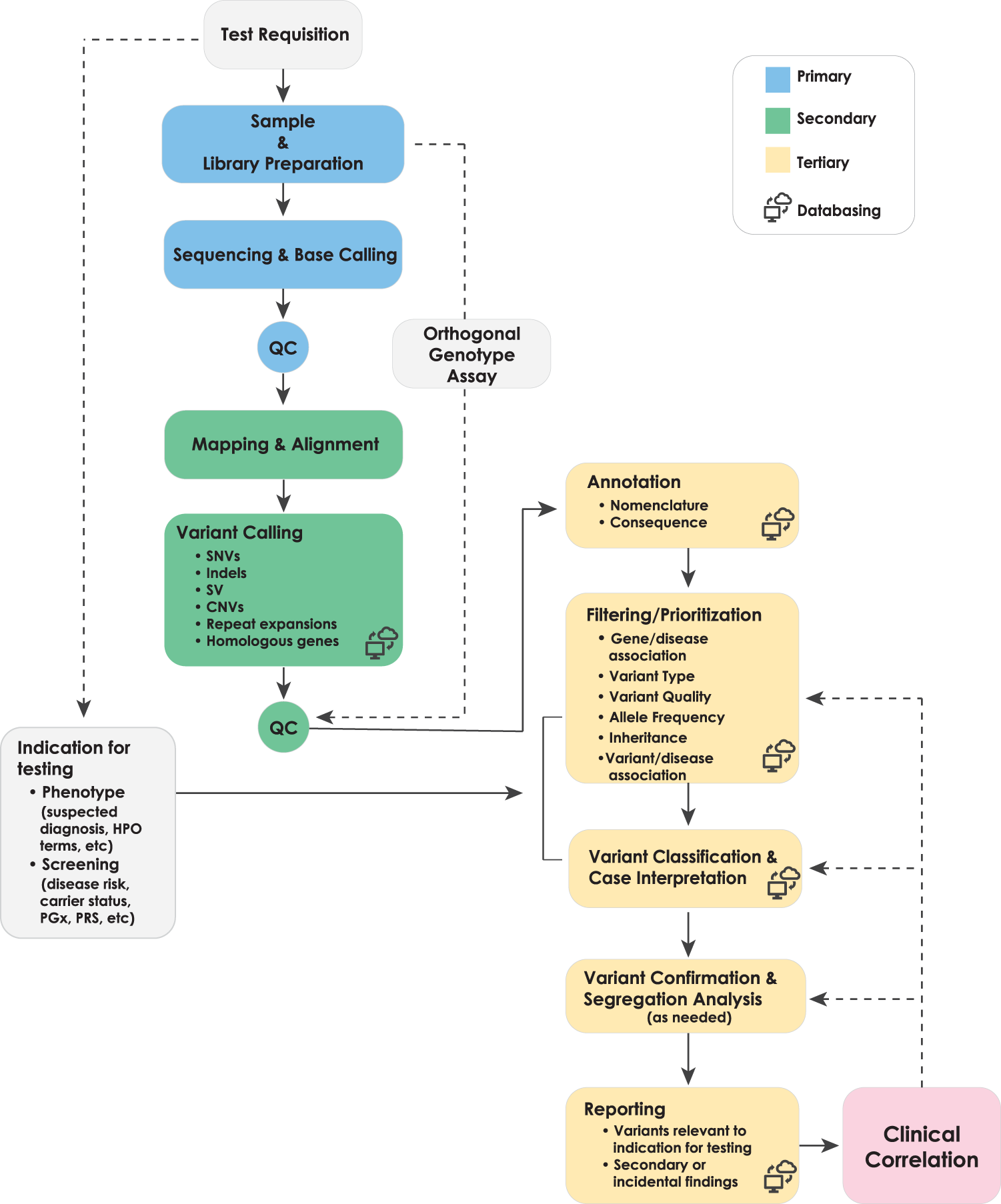
Best practices for the interpretation and reporting of clinical whole genome sequencing | npj Genomic Medicine
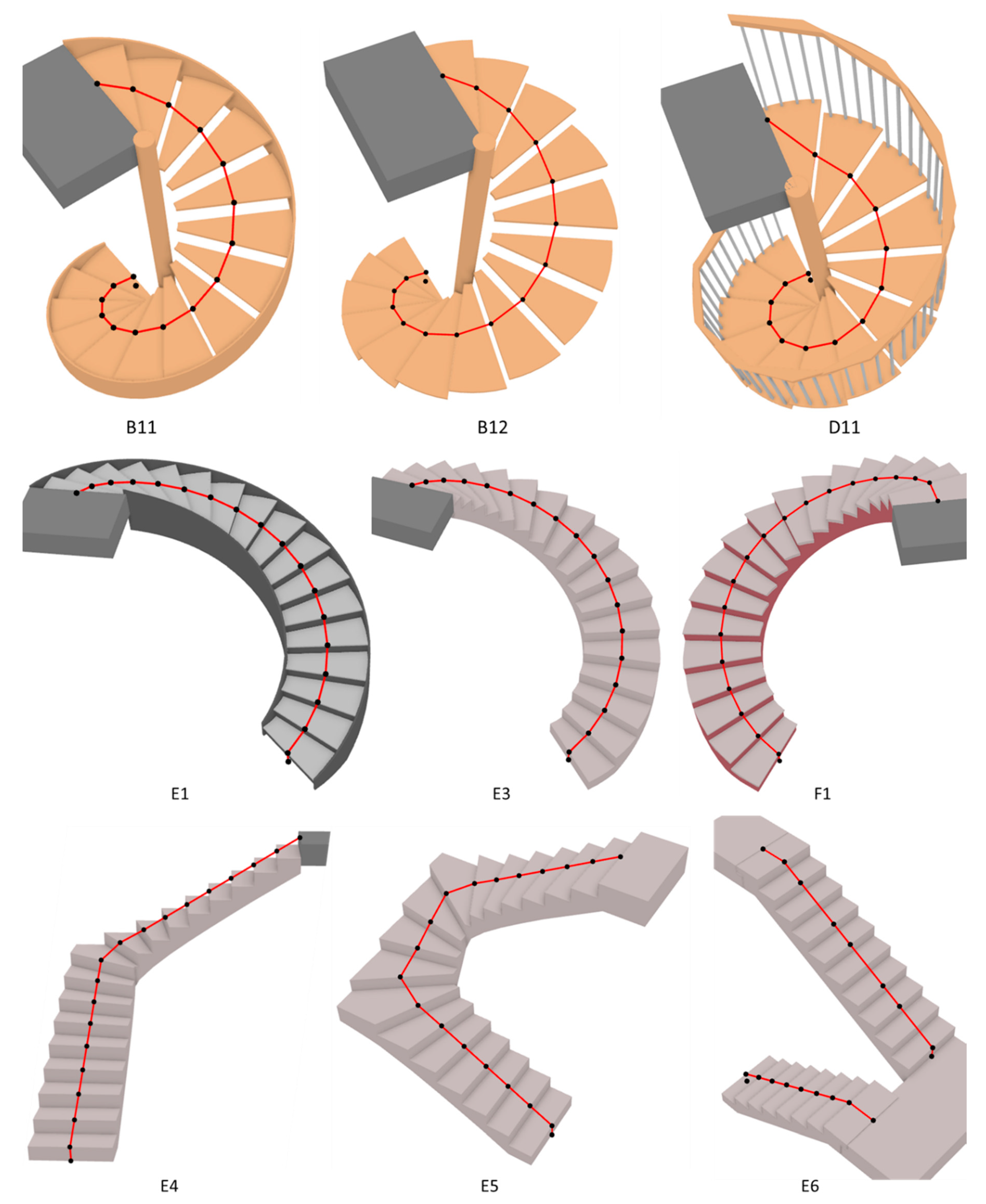
IJGI | Free Full-Text | Automatic Generation of High-Accuracy Stair Paths for Straight, Spiral, and Winder Stairs Using IFC-Based Models
![Amazon.com: KCT [2 PACK] Paperfeel Screen Protector Compatible with iPad Pro 11 Inch (2022 & 2021 & 2020 & 2018 Model) / iPad Air 5th & 4th Generation (10.9 inch, 2022 & Amazon.com: KCT [2 PACK] Paperfeel Screen Protector Compatible with iPad Pro 11 Inch (2022 & 2021 & 2020 & 2018 Model) / iPad Air 5th & 4th Generation (10.9 inch, 2022 &](https://m.media-amazon.com/images/I/71zcW4CVYgS._AC_UF1000,1000_QL80_.jpg)
Amazon.com: KCT [2 PACK] Paperfeel Screen Protector Compatible with iPad Pro 11 Inch (2022 & 2021 & 2020 & 2018 Model) / iPad Air 5th & 4th Generation (10.9 inch, 2022 &
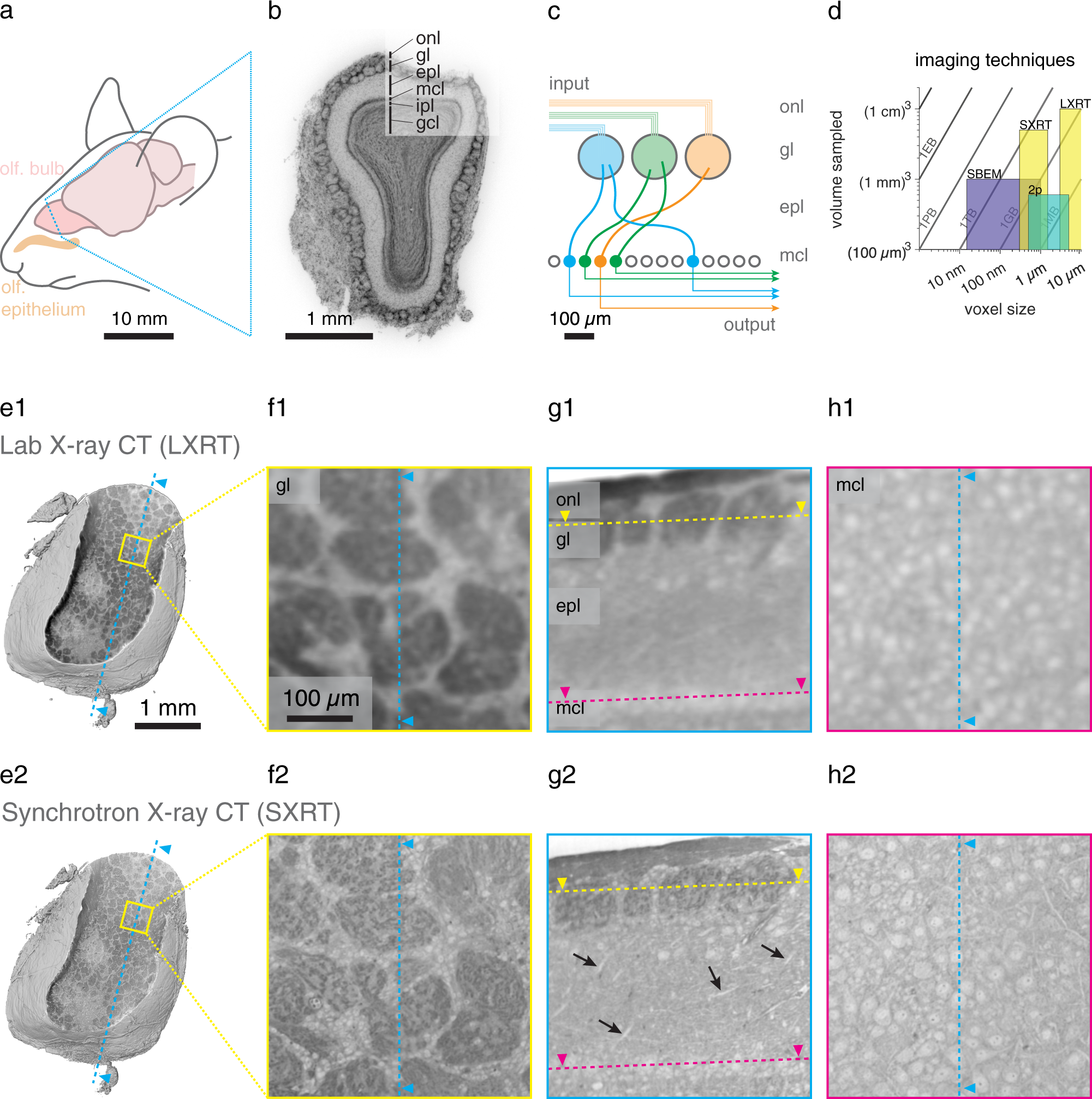
Functional and multiscale 3D structural investigation of brain tissue through correlative in vivo physiology, synchrotron microtomography and volume electron microscopy | Nature Communications

PyCGTOOL: Automated Generation of Coarse-Grained Molecular Dynamics Models from Atomistic Trajectories | Journal of Chemical Information and Modeling

Generative Network Complex for the Automated Generation of Drug-like Molecules | Journal of Chemical Information and Modeling

![PDF] Automatic generation of suggestions for program investigation | Semantic Scholar PDF] Automatic generation of suggestions for program investigation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da78db4b0a02c3c7dfb95367eb4927a0e0eda79d/8-Table6-1.png)

![PDF] Automatic generation of suggestions for program investigation | Semantic Scholar PDF] Automatic generation of suggestions for program investigation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da78db4b0a02c3c7dfb95367eb4927a0e0eda79d/6-Table2-1.png)


![PDF] Automatic generation of suggestions for program investigation | Semantic Scholar PDF] Automatic generation of suggestions for program investigation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da78db4b0a02c3c7dfb95367eb4927a0e0eda79d/8-Table4-1.png)
![PDF] Automatic generation of suggestions for program investigation | Semantic Scholar PDF] Automatic generation of suggestions for program investigation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da78db4b0a02c3c7dfb95367eb4927a0e0eda79d/7-Figure6-1.png)